Exfiltrating Data Using DNS
I have been learning more about exfiltrating data using DNS requests at ine.com
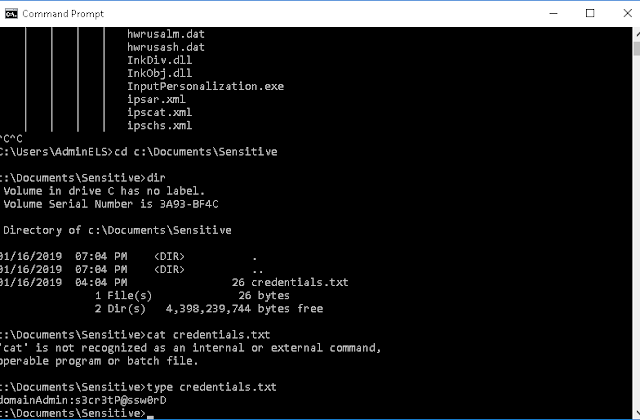
After connecting to the lab machine, my first job was to find sensitive data. I used tree c:\ /f | more to look through the directories. The first thing I saw was a directory called sensitive with a .txt file called credentials inside it. I had a look at this using the type command (after trying cat as I'm so used to Linux!)
I now needed to find a way to exfiltrate this data and bypass any egress filtering. I started by checking if any common ports were allowed for outbound connections. To do this, I used sudo python3 -m http.server 8080
I then used the browser on the target machine to try to connect to my simple HTTP server. I tried this using ports 80, 8080, 443 and 8443. I discovered that only port 8080 was allowed to access the public internet.
Next, I wanted to see if DNS lookups could be made from the target machine. To do this, I first of all had to reconfigure the DNS server on the target machine to be my attacking machine.
I then opened Wireshark on my attacking machine and filtered it for DNS traffic before performing an nslookup command on the target machine.
The DNS record requests which showed up in Wireshark let me know that DNS lookups were indeed permitted from the target machine. I therefore set up another Python3 http.server on port 8080 and served Packet Whisper to the target machine. I started a Wireshark capture on my attacking machine. I then ran Packet Whisper on the target machine and after using the default ciphers I transferred the data back to my attacking machine using DNS lookups.
The transfer completed successfully! I next saved the Wireshark capture as a .pcap file and decrypted it. The exfiltration had been successful!The final part of the challenge was to find a way to automate the process of finding other ports which might be open and therefore available for use as a means to exfiltrate data from the target machine. To do this, I used the egresscheck-framework Python program from Github.
I used a Python3 http.server to serve the above Powershell script to the target machine using the .bat file it had been saved in. I then started a Wireshark capture on my attacking machine and executed the .bat file as an administrator on the target machine. I looked through the Wireshark capture once the Powershell script had ended and found a connection from port 9000.
I enjoyed learning more about data exfiltration using DNS lookups as it is a sneaky way to bypass egress filtering! :-)