Cain and Abel (MITM)
The aim of this lab was to gain a better understanding of man in the middle attacks and the (outdated) tools Cain and Abel.
To start with, I used Remote Desktop to connect to an auditing machine on the target network. Cain was already installed on the machine, so I fired it up and started an ARP scan of the network. Wireshark shows that these ARP requests were sent to all of the machines on the subnet as they were sent to the ff:ff:ff:ff:ff:ff broadcast address.
My next task was to launch a man in the middle attack against the machine @ 172.16.5.5 and its default gateway @ 172.16.5.1
This attack tricks the two targeted machines into sending their data to my attacking machine which allows me to view and / or edit the data before passing it on to the correct destination - a man in the middle attack. This works because we are able to send gratuitous ARP replies in which we tell a machine that our MAC address is at a specified IP. When we do this to two different machines, telling each one that our MAC is at the IP of the other machine, we effectively become the man in the middle. We need to ensure that we enable IP forwarding on our attacking machine first so we do not cause a denial of service to the targeted machines. In this attack, our MAC address is added to the ARP cache of the targeted machines. The ARP cache contains a Time To Live so we need to keep sending the fake IP / MAC data until we want to end the poisoning attack.
I then generated some traffic to replicate a user on the remote machine.
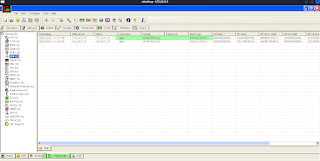
Next, I stopped the attack and had a look to see which credentials had been captured. I found credentials for FTP, HTTP, RDP and VNC (a tool to remotely administer a machine).
The RDP credentials were stored in a .txt file by Cain. The keystrokes had been logged so they revealed the plain text password. The VNC password was hashed using 3DES. This was sent to Cain's Cracker tool. The dictionary attack did not work, but a brute force attack using 5 characters discovered the plain text password.
I next looked for the .RDP files which contain encrypted passwords. I found these and then used Cain's Remote Desktop Password Decoder tool to crack them.
Next, I experimented with Cain's NTLM hash cracker tool. First of all, I imported the hashes from the local machine to Cain. Next, I launched a dictionary attack against them.
After this, I launched an ARP poisoning attack against the machines @ 172.16.5.15 and 172.16.5.10
After a while, I stopped the attack and found some SMB credentials had been intercepted. I was able to crack these with a dictionary attack.
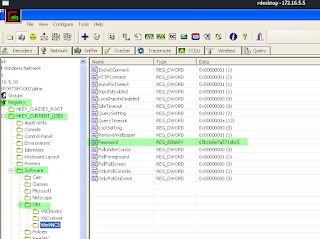
Now that I had these credentials, I could connect to the remote machine using them. I then looked for the encrypted VNC password which is stored in the Windows registry. Once I had located it, I used Cain's VNC Password Decoder tool to crack it.
I could now use VNC to access the remote machine, but I installed Abel instead. Once Abel had been installed, I used it to open a command prompt on the remote machine.
I looked to see if port 3389 was listening for RDP connections - it was not. I therefore enabled RDP and then checked the firewall to see if port 3389 was open - it was not. I opened port 3389 for RDP connections and then tried to RDP onto the machine. This was successful now that the service had been enabled and the firewall amended.
Finally, I tried to access the admin area of the organisation's website using the looted http credentials. This was successful.