Hacking WordPress
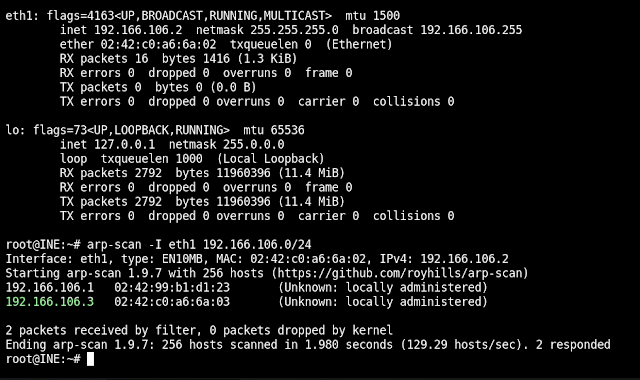
The goal of this lab was to hack into a WordPress blog and recover the flag. I started by using arp-scan to find live hosts. Once I had identified one, I used nmap to scan for open ports. Nmap discovered that only port 80 was open, so I then probed port 80 more aggressively and discovered that a WordPress powered website was being served on it.
Lots of attacks against WordPress rely on taking over an administrator account, so I wrote a bash script to enumerate users on the website. This script simply iterates through the numbers 1 to 50 and checks them in the ?author parameter. We can also do this using a list of potential user names, but I find using numbers is more reliable. This enumeration discovered that the default admin account was being used on this website.
The next step was to brute-force the password. This can be done using WPScan along with this command wpscan --url http://demo.ine.local --passwords /home/user/passwords.txt but WPScan was not installed on the attacking machine so I used Burpsuite's Intruder tool instead. I found the password to be Lawrence based off the difference in the size of the responses to the different passwords. This worked and I therefore had compromised an admin account.
My next job was to somehow use this compromised account to get a reverse shell on the server hosting it. My first port of call was the installed plugins, as they often have vulnerabilities in them since they are open source. I discovered that the installed plugin called Responsive Thumbnail Slider was a version (1.0) which was vulnerable to an arbitrary file upload attack. The proof of concept seemed simple enough, so I gave it a go using a PHP script as a payload since WordPress uses PHP.
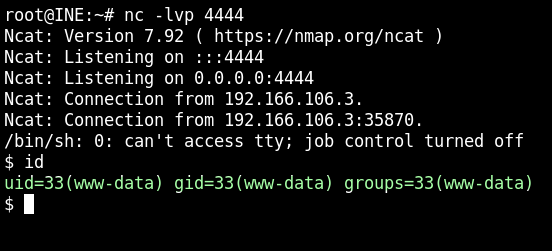
This attack was successful. I tested it by using a simple Linux command (id) as the cmd parameter in the URL at the path to the uploaded malware. I then crafted a reverse shell bash script, URL encoded it, fired up a netcat listener and then used the encoded script as the cmd parameter. This gave me a reverse shell. I was then able to find and read the flag.
The lab was now completed, but I wanted to explore hacking WordPress websites more.
It is not always the case that we will find a vulnerable plugin already installed on the site, so I started to look into other ways to gain shells using compromised admin accounts. The first way I tried was to craft a meterpreter_reverse_tcp shell using msfvenom and then upload it as a new plugin. This worked, even though an error message was returned. The .php shell was still uploaded to the /wp-content/uploads/2022/03 directory so I was able to start a handler using msfconsole and then navigate to the uploaded malware to trigger a meterpreter session.
Another technique I tried was editing an installed plugin. To do this, I added a line of code at the top of the .php file which would request the command passed to it using puzz00 as a parameter. I put this into an if statement so it would only work if the puzz00 parameter was set. This worked when tested with a simple bash command. I found I needed to use a python reverse shell with this technique.
The last technique I tried was to create a new plugin. The comments are important as they flag to WordPress that the file is a plugin. The file had to be zipped before being uploaded. It was then just a matter of visiting the path to the new plugin in order to use the malware. Again, I found the python reverse shell worked well.