Enumerating DNS Servers
The goal of this lab on ine was to enumerate the DNS server to discover as much as possible about the domain witrap.com
In my other (first) post about enumerating DNS servers (Information Gathering Lab) I mentioned that I would show how we can brute-force subdomains and look for machines which only respond to reverse DNS lookups. These techniques are covered in this post.
My first job was to find out more about the network my attacking machine was connected to. The ip addr command revealed that it was on a /24 network 192.36.208.0/24 The IP address of the attacking machine was 192.36.208.2
I decided to start off by using nmap to perform an ICMP scan. I followed this up with a fast half-open SYN scan as sometimes ICMP traffic is blocked or dropped by firewalls.
I then specifically targeted DNS servers by performing a UDP scan against port 53 and then another half-open SYN scan against port 53 but with the --source-port switch set to 53 as sometimes DNS servers will only accept traffic coming from port 53. I then prepared a txt file of live hosts with port 53 open - only the machine @ 192.36.208.3 was visible. This suggested to me that this machine was the DNS server I could use to further enumerate the witrap.com domain and its subdomains.
I started off by using dig to find the A record (IPv4 address) for the domain name witrap.com
I then decided to try to find subdomains by writing a bash script which brute-forced its way through a top 20,000 subdomains name file. This method discovered a number of subdomains for the domain witrap.com along with their IPv4 addresses.
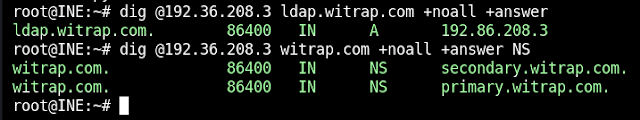
One of the questions posed in the lab challenges was to find the IP address of the machine using LDAP over TCP. I had already discovered this as 192.86.208.3 but to make it more clear I performed a simple dig request against the subdomain ldap.witrap.com I also wanted to make the name servers more clear, so I did a dig request for the NS records for the domain witrap.com and then retrieved their IPv4 addresses using the +short flag.
I was quite happy with all the information I had found, but I thought I would try a zone transfer to see if that would be possible and if I had missed anything. The zone transfer worked due to a misconfiguration - zone transfers should only be allowed for trusted IP addresses (secondary name servers) so that they can keep up to date records. Anyway, I found that my earlier enumeration had found all the A records for the subdomains. The zone transfer did show that an alias (open.witrap.com) was being used for free.witrap.com This was shown as a CNAME record. I also found a secret flag in the TXT record of a machine which I had not been able to find due to its name not being in the txt file I had used to brute force the subdomains th3s3r3tflag.witrap.com
The last two challenges for this lab were to do with the reverse zone. The first of these challenges was to find a subdomain which was only listed in the reverse zone, and the other challenge was to find all the records except the Start Of Authority ones in the reverse zone.
In order to solve these problems, I created a short Python program to write all the possible IP addresses into a txt file. This was possible because the challenge let me know that I would need to work in the 192.168.x.x netblock.
I then used a bash script to check all of these possible IP addresses for subdomains in the reverse zone by using the -x flag of dig. This successfully found answers to the last two challenges. The new subdomain was temp.witrap.com @ 192.168.62.118
Since zone transfers were possible, I tried this method to see if I could find any other results. I was happy to see that my bash script method had indeed found everything.
Essentially, this lab had been completed at this point, but I decided to create a mindmap using VYM.
The next stage would be to enumerate the machines on the 192.36.208.0/24 network to find open ports and vulnerabilities. This was not the goal of this lab, but I did have a quick look at one machine which had stood out to me during the initial nmap half-open SYN scan. This particular machine had ports 139 and 445 open. I had to reconnect to the lab, as I had taken a break and the lab had closed during that time, so the IP addresses in the following pictures are different to those seen so far.
I first of all used nmblookup -A 192.51.164.8 to see if the machine was serving anything - it was - as indicated by the code <20>
I tried a null session attack to see if I could find any shares without needing a password by using smbclient with the -N flag to specify no password and the -L flag to list any shares. As I was working from a command line in Linux, I had to escape back-slashes.
The public share looked interesting, so I tried to connect to it with no password. This worked and I was able to find a directory called secret in which there was a flag.
This was a nice find, so I got it and had a look.
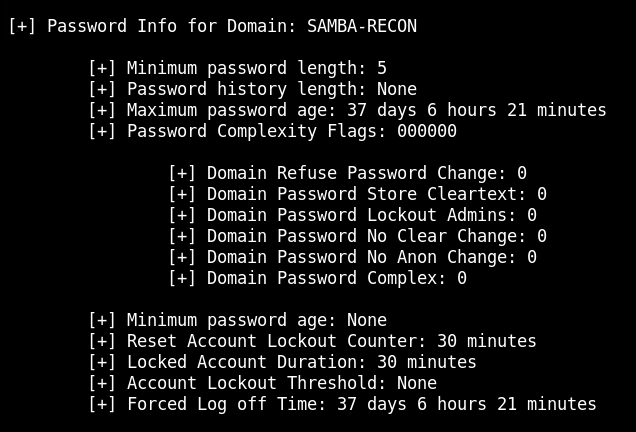
I finished my work in this lab by using enum4linux against the machine @ 192.51.164.8 It found some usernames, local and domain groups, a little about the password policy for the SAMBA-RECON domain as well as verifying what I already suspected about the other shares - none of them would allow passwordless access.
Thanks to ine.com for the lab - it was fun to complete.
I was happy to see that my brute-forcing methods of enumeration found the same information which the zone transfers provided (except for the secret flag machine!) It was also nice to find a bonus flag at the end :-)
Thanks for reading - puzz00